We’ve lived almost all our lives in a password cycle: create them, forget them, reset them, rinse and repeat. Logins become a memory test, not the identity safeguard they should be. Despite all this effort, we are not any safer. An attacker does not need to guess your complex password—a keylogger or phishing email can capture your password, and if attackers are patient, your password could be leaked in the next breach. We live in an era where a single password can unlock decades of one’s digital life, making traditional authentication options feel outdated.
Passkeys offer a way out. Instead of remembering a secret, your device proves your identity securely and uniquely for different accounts. They eliminate the risk of password reuse, typing errors, or guessing, making logging in effortless and as close to unbreakable as anything we’ve seen. Finally, you’ll worry less about how often you should change your password.
The password problem we’ve been stuck with
Even strong passwords fail against modern-day attacks
If complexity equals safety, then it makes perfect sense that we have spent decades mixing symbols, numbers, and uppercase letters to create the strongest passwords. Regardless of how complex they are, passwords are still a big vulnerability. They are static and can be copied, stolen, or leaked. Once they fall into the wrong hands, the damage spreads across all accounts using the same formula.
Because of how frequently we see data breaches, changing passwords feels less like a security measure and more like a routine chore. Your strongest passwords may still end up in a database that hackers can access, and two-factor authentication (2FA) is susceptible to phishing and only serves as a bandage, not a solution.
The password model is actually the problem. The paradox is that security can’t fix the fundamental problem: passwords force you to share a secret that is repeatedly reused. Rather than finding ways to remember stronger passwords, we need a solution that completely eliminates the need for them.
What makes passkeys different (and brilliant)
A login method that proves who you are without revealing anything
Passkeys use cryptographic proof to replace static, guessable passwords. Instead of memorizing a secret, your device creates a public and a private key. The public key resides on the servers of the service you sign in to—Google, your bank, or any other service—while the private key remains on your device. This mathematically linked unique pair is impossible to reverse-engineer.
At login, the website sends a challenge that your device signs with its private key, proving your identity without revealing the secret. This entire process is invisible to you, even though you authenticate using a PIN, Face ID, or Touch ID.
The structure of passkeys completely breaks the attack chain. It leaves nothing for a hacker to intercept, nothing to phish, and no details that can be reused on another website. Passkeys are bound to your hardware, and each one is unique to an account, making even full database leaks useless for an attacker attempting to impersonate you.
While passkeys are resistant to many attacks, you should still keep device recovery options and backups in place, as losing the device without recovery may lock you out.
Passkeys fix everything passwords broke
Immune to phishing, leaks, and password reuse by design
Where passwords depend on your discipline and fail, passkeys succeed by removing the human variable completely. You cannot mistakenly type them into fake pages or reuse them across several websites, and they never show up in plain text. Even when a website is compromised, the public key on the server is useless without the matching private key on your device.
You do not manually enter the passkey, so the browser can only complete this cryptographic handshake with the domains it verifies, leaving no chance for a phishing attack. In cases where the attacker creates a perfect clone of the website, the authentication will fail unless the URL exactly matches the domain registered with the passkey.
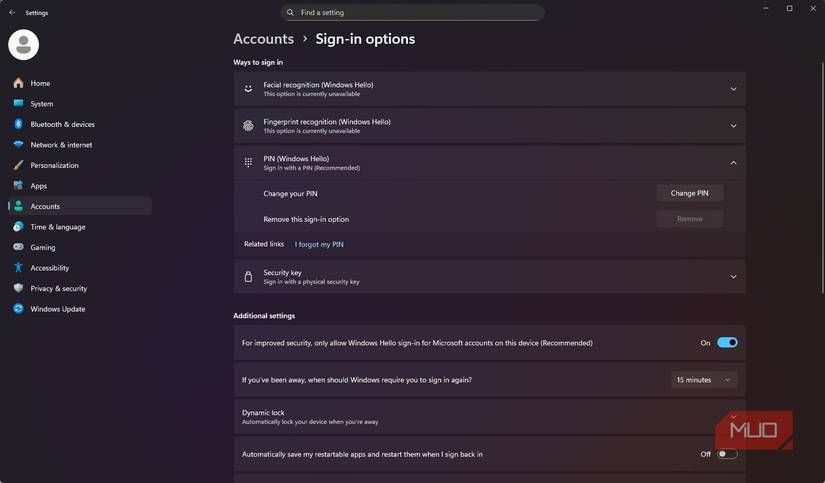
Device theft is also less of a concern because the private passkeys are secured in the Trusted Platform Module (TPM). This secure enclave is protected by your biometrics and a hardware-backed layer, making it inaccessible without your fingerprint or face. This model relies on a simple act to confirm your presence rather than remembering or guessing. However, physical device loss still requires quick user action (e.g., device wipe) to prevent a potential attack if biometrics or PINs are compromised.
TPM (or Secure Element/Enclave) is the mechanism used by devices—Windows, Android, and Apple’s Secure Enclave—to protect key material.
The future without passwords
Big tech is already shifting; you should, too
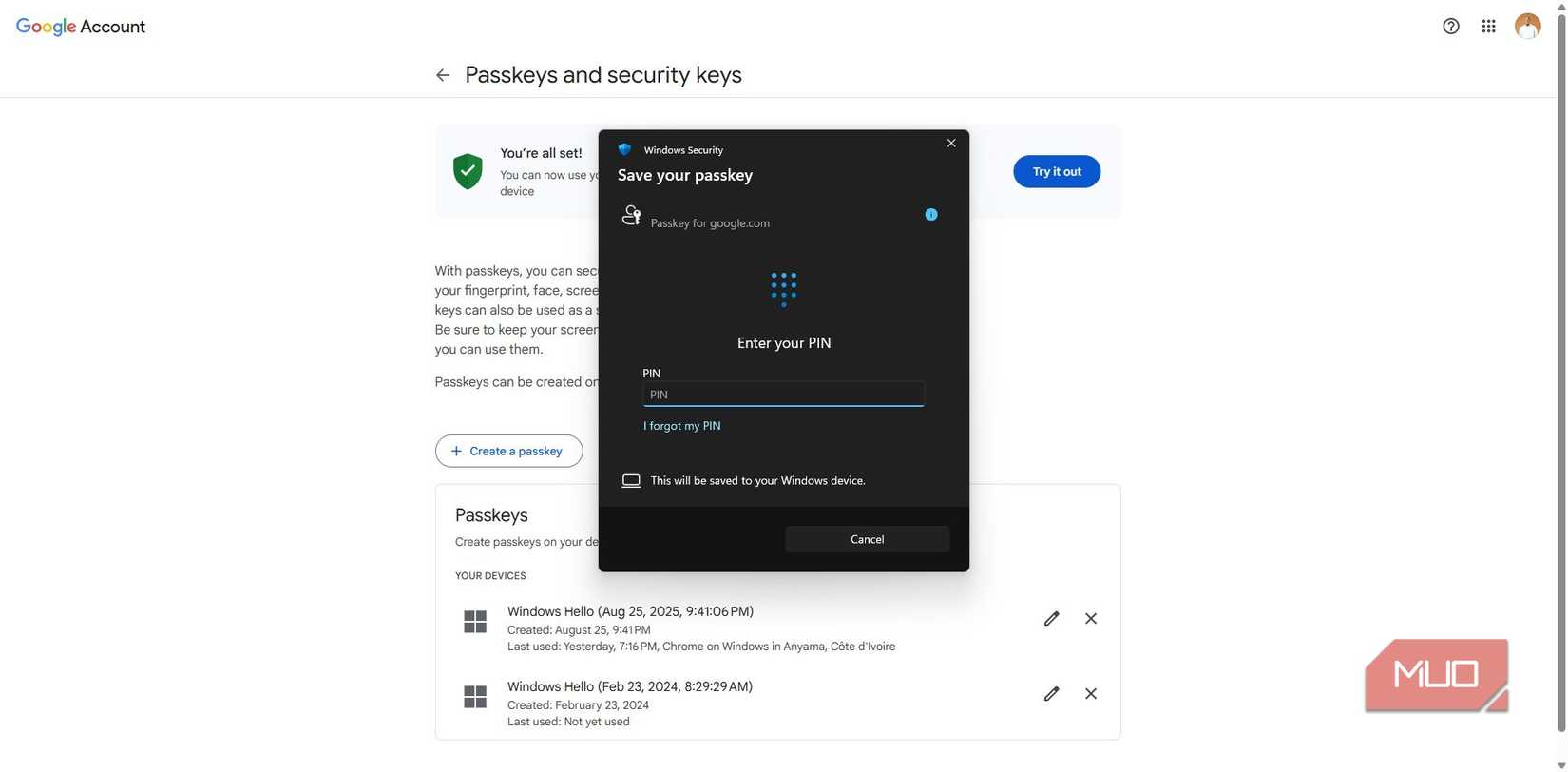
Passkeys are the new standard, and their mass adoption clearly points to this. Big tech, including Apple, Google, and Microsoft, is rallying behind the new system, which shows it’s not a passing trend—it’s time to start using passkeys. These three organizations have passkey integration across browsers, cloud sync systems, and devices. Big organizations, including PayPal, Best Buy, eBay, and Google Accounts, now let you sign in via Face ID, Touch ID, or Windows Hello, not just the traditional password.
This makes the system usable today: you can choose the “Sign in with a passkey” option. Even established password managers, like 1Password and Dashlane, are adopting the new tech, syncing these encrypted credentials between your devices.
No matter how slow this transition is, the end result will be invisible authentication that removes the burden of thinking about sign-ins, as login security becomes an automatic part of the device that just happens.
The era of passwords is ending: here is what comes next
Without fanfare, passwords are fading away. Passkeys represent the shift in online identity verification that makes security harder to breach while remaining virtually invisible. Logins become handshakes between services and devices, replacing typing and reducing the risk of exposure.
There are architectural differences between passwords and passkeys. Passkeys are considered the strongest form of Phishing-Resistant MFA (PR-MFA), so as long as the option is available, you should always choose passkeys and embrace the future of online security.
Source link