TL;DR: Experience the internet ad-free forever with this lifetime subscription to AdGuard Family Plan, on sale now for just $39.99 (reg. $169.99). We’ve all been there — minding our own business, browsing the web, when out of nowhere, a loud video ad blares and you can’t find the mute button fast enough. If you’d like to enjoy a more peaceful …
Read More »Tag Archives: malware
Cisco ASA Firewall Zero-Day Exploits Deploy RayInitiator and LINE VIPER Malware
The U.K. National Cyber Security Centre (NCSC) has revealed that threat actors have exploited the recently disclosed security flaws impacting Cisco firewalls as part of zero-day attacks to deliver previously undocumented malware families like RayInitiator and LINE VIPER. “The RayInitiator and LINE VIPER malware represent a significant evolution on that used in the previous campaign, both in sophistication and its …
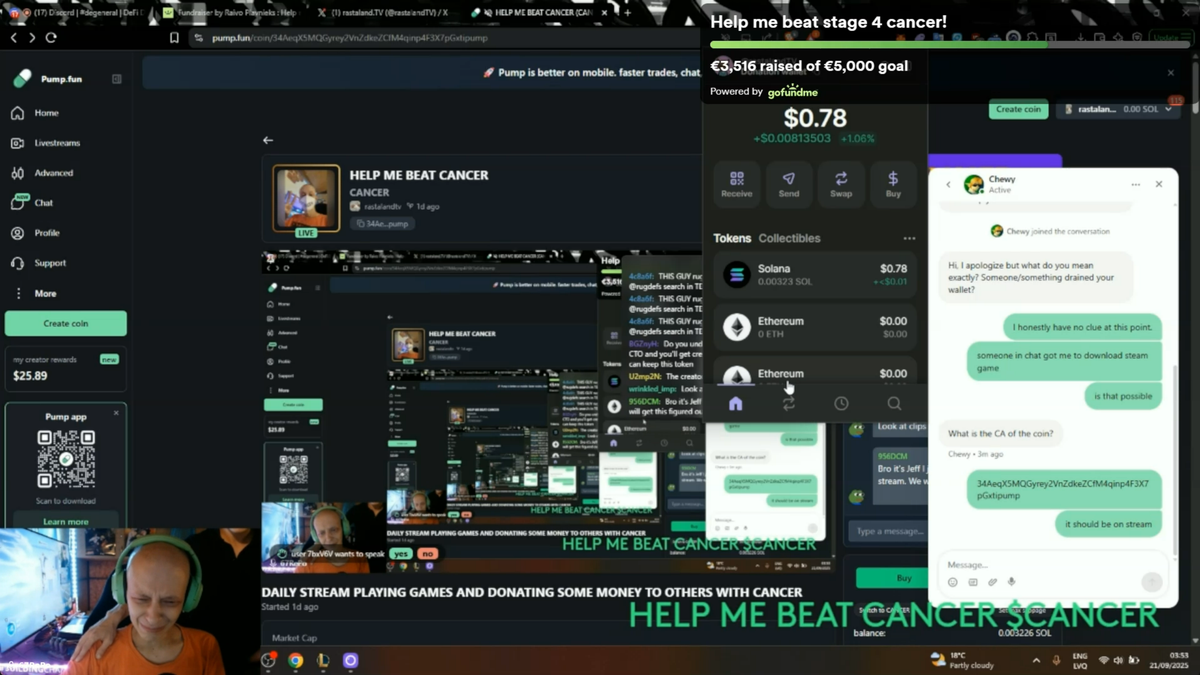
Read More »Malware ‘Game’ On Steam Stole $32K From Cancer-Stricken Streamer
Given the endless waterfall of garbage that arrives on Steam, it might seem like you can upload and sell absolutely anything on the storefront. However, there are meant to be some verification checks in place to prevent the most egregious examples of nefarious content from reaching the platform—it’s just it doesn’t always work. Hence BlockBlasters, a Trojan-Horse 2D platformer that …
Read More »Steam Hosted Malware Game that Stole $32,000 from a Cancer Patient Live on Stream
A cancer patient lost $32,000 in crypto after installing a Steam game on his computer containing malware that drained one of his crypto wallets. Raivo Plavnieks is a 26 year old self-described “crypto degen” from Latvia who streams on the site Pump.fun under the name Rastaland. After a seven hour stream on September 20, Plavnieks logged off and cashed out …
Read More »CISA exposes malware kits deployed in Ivanti EPMM attacks
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published an analysis of the malware deployed in attacks exploiting vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM). The flaws are an authentication bypass in EPMM’s API component (CVE-2025-4427) and a code injection vulnerability (CVE-2025-4428) that allows execution of arbitrary code. The two vulnerabilities affect the following Ivanti EPMM development branches and …
Read More »Google nukes 224 Android malware apps behind massive ad fraud campaign
A massive Android ad fraud operation dubbed “SlopAds” was disrupted after 224 malicious applications on Google Play were used to generate 2.3 billion ad requests per day. The ad fraud campaign was discovered by HUMAN’s Satori Threat Intelligence team, which reported that the apps were downloaded over 38 million times and employed obfuscation and steganography to conceal the malicious behavior from Google …
Read More »Silver Fox Exploits Microsoft-Signed WatchDog Driver to Deploy ValleyRAT Malware
The threat actor known as Silver Fox has been attributed to abuse of a previously unknown vulnerable driver associated with WatchDog Anti-malware as part of a Bring Your Own Vulnerable Driver (BYOVD) attack aimed at disarming security solutions installed on compromised hosts. The vulnerable driver in question is “amsdk.sys” (version 1.0.600), a 64-bit, validly signed Windows kernel device driver that’s …
Read More »Brokewell Android malware delivered through fake TradingView ads
Cybercriminals are abusing Meta’s advertising platforms with fake offers of a free TradingView Premium app that spreads the Brokewell malware for Android. The campaign targets cryptocurrency assets and has been running since at least July 22nd through an estimated 75 localized ads. Brokewell has been around since early 2024 and features a broad set of capabilities that include stealing sensitive …
Read More »A disgruntled worker built his own kill-switch malware to take down his former employer – and it didn’t pay off
A software developer sabotaged his employer after being demoted Davis Lu created a “kill switch” that would lock out all users He was sentenced to four years in jail and additional three years of supervised leave A disgruntled worker has been sentenced to four years in prison after installing “kill switch” malware on his employer’s network which was set to …
Read More »APT36 hackers abuse Linux .desktop files to install malware in new attacks
The Pakistani APT36 cyberspies are using Linux .desktop files to load malware in new attacks against government and defense entities in India. The activity, documented in reports by CYFIRMA and CloudSEK, aims at data exfiltration and persistent espionage access. APT 36 has previously used .desktop files to load malware in targeted espionage operations in South Asia. The attacks were first …
Read More »