Although some sources are wary about using two-factor authentication (2FA) to secure your online accounts, it remains a worthwhile consideration when setting up a new account.
It’s like, why make it easy for someone to take over your account after your password was purposely cracked or exposed?
2FA requires the person to go through an extra step to gain entry. But what no one tells you is that your 2FA method (or methods) is what matters most.
Using a dedicated 2FA authenticator app is more secure than using your phone number as a 2FA authenticator. That’s because the phone number method uses SMS, which has weaker security and becomes easier to exploit.
Whether you own a premium phone from Google or a budget option from Motorola, weak account security practices can still compromise your account.
Here’s what you need to know before considering using your phone number for 2FA.

Related
Why Gmail’s switch from SMS authentication to QR codes should be the standard
QR code authentication is better in every way
6
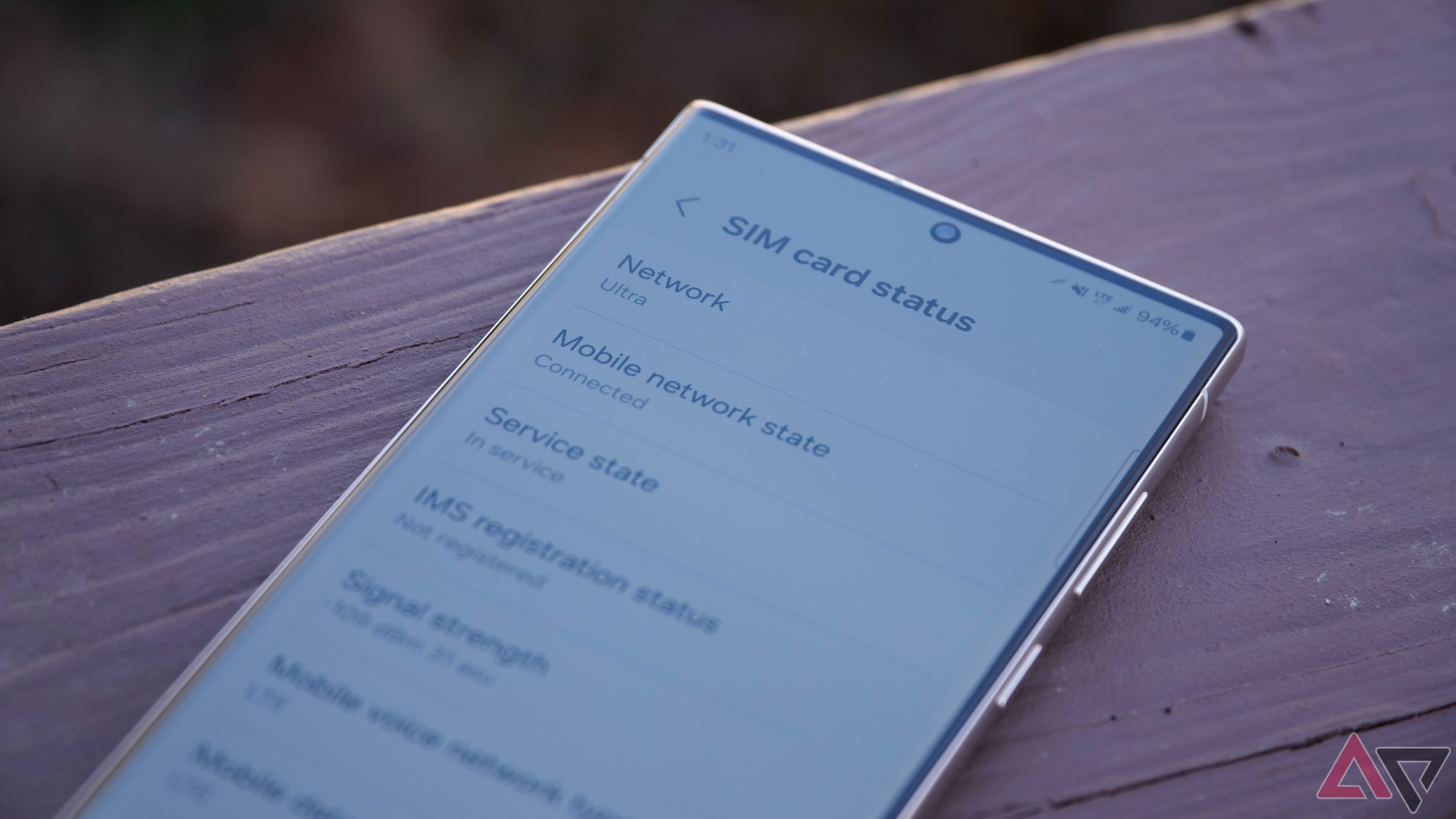
Know the trustworthiness of your carrier and device
It can lead to situations that are difficult to control
Even if you are careful, other factors can lead to detrimental consequences of having your codes, accounts, and personal information stolen by malicious actors.
For example, if your carrier lacks effective practices for verifying your account and number, you can still fall victim to fraudulent activity.
Bad actors have become increasingly skilled at social engineering situations where the carrier willingly complies with a disguised actor’s demands to gain access.
You see this with SIM swapping. The transferred SIM card becomes fully controlled by the scammer. Carriers can prevent this by implementing security measures.
Carriers can promote additional security measures, such as SIM lock features and port freeze options, along with requiring unique passcodes that are separate from the general account passwords.
0:56

Related
How to enable SIM lock on your Android phone
Prevent malicious SIM card use by adding an extra layer of security
AT&T, for example, introduced an account locking feature to protect wireless users against SIM swapping attacks.
It’s a feature you can activate within the AT&T app, which prevents unauthorized users from changing phone numbers, transferring SIM cards, and modifying billing information without further authorization.
Other carriers, such as T-Mobile and Verizon, have introduced a similar feature to address the same issue.
Another factor is your device. If your device has malware on it, your data is in great danger.
Anything that is sent to your device is there for the taking through these installed malware programs.
Malicious actors will use infostealing logs to gather information, either to use it for their gain or to sell it on the Dark Web.
These logs can contain a variety of information, including your login information, scraped SMS messages, and session cookies.
Your device is a gold mine for personal data; it may hold all your financial details, deeply personal information, and more. So always check if your device has been infected with malware before trusting it.
5
Be aware of SIM swapping
It is a type of account takeover that targets weak 2FA
SIM swapping is a significant issue that exploits the weakness of 2FA. SIM swapping is a type of fraud in which a scammer gains unauthorized control of a victim’s phone number through their chosen carrier.
The scammer persuades the carrier service (usually through impersonation) to transfer the number to a new SIM card, which they use to intercept incoming calls, messages, and authentication codes.
This means that the hacker doesn’t need the physical phone to access those SMS codes — this type of attack is known as an SS7 attack.
SIM swapping is a catalyst for account takeovers. Any account that is locked behind two-factor authentication using a phone number is now fair game to the malicious actor.
For example, when your online banking information is linked to your phone number, scammers who have SIM-swapped can now gain access to your account and steal your financial information.
SIM swapping is more common than you might think, and when it occurs, the damage can be almost irreversible.
4
SMS codes are easier to exploit
This type of text messaging service lacks robust security
Source: Verizon
SMS codes, which are the codes you receive via text messages when setting up 2FA using a phone number, are not well-protected.
SMS messages are not end-to-end encrypted, meaning they can be intercepted by third parties while traveling through the network. The codes themselves can be read just before they reach your phone.
SMS also relies on mobile networks. If those mobile networks have security vulnerabilities, hackers can potentially exploit this and use techniques like SIM swapping and SS7 attacks to intercept those codes.
3
Phone number recycling can leave behind traces
It gives unintended access to old accounts
Old phone numbers can resurface. However, hackers can use this information to identify numbers associated with accounts.
Phone number recycling refers to the practice of a carrier or service reusing a deactivated number and then assigning it to a new user.
Before these numbers are recycled, telecom providers wait a period before reusing them. This process typically helps mitigate costs and address the issue of phone numbers being a finite resource.
Hackers exploit phone number recycling. When a hacker obtains a recycled number, they can use it to locate linked accounts, especially if the previous owners did not deactivate or wipe this information. Moreover, the new owner could also inadvertently inherit those accounts.
When you log in to accounts without updating your phone number, the new owner will receive the code in your stead.
Your carrier may warn you to disconnect your old number to connected online accounts within the deactivation period.
2
Your phone number is only the start
Scammers can data-mine more personal information
Source: Lucas Gouveia/Android Police | Macrovector/alexdndz/Shutterstock
There’s a real chance that your phone number has already been leaked and is now available on the Dark Web. It doesn’t stop there, as it can mean that other personal information can also be present.
Malicious actors can use that to trace back to your identity and use that to mine recent data breaches/data broker lists to get hold of more of your data.
Eventually, that data can lead to other scams, account takeovers, and, worse, identity theft.
1
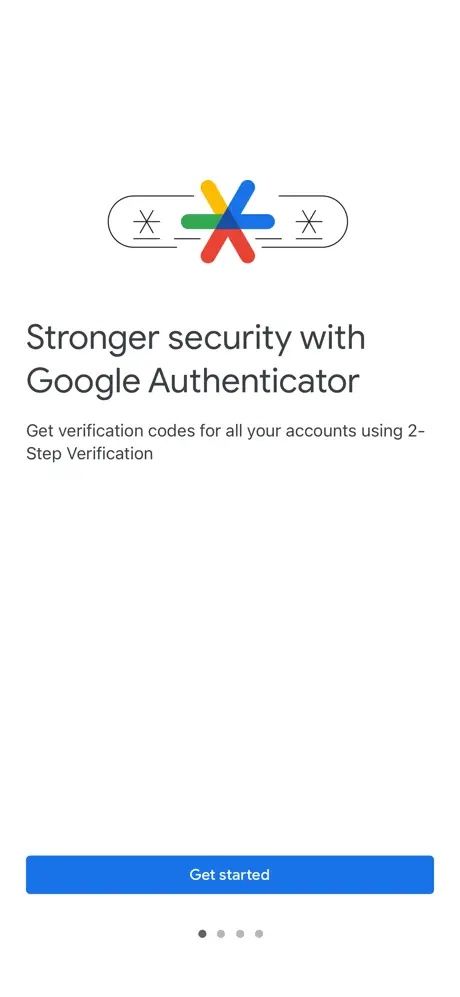
Consider other more secure 2FA options
You don’t have to rely on SMS 2FA
While SMS-based 2FA methods are convenient (as outlined in the other entries on this list), they also introduce unwanted vulnerabilities.
Authenticator apps essentially do the same thing as SMS (phone number) 2FA, but are significantly more secure.
Two common options that are easily accessible and considered trustworthy are Google Authenticator and Microsoft Authenticator.
Authenticator apps generate codes locally on your device, unlike SMS, which can be intercepted from a network. You can access these codes offline, and they refresh more quickly than SMS-based ones.
You also don’t need to give your phone number. Instead, you download an app and connect it to your account.
After you’ve synced the app to the website or service, you input the code every time you log in.
Another alternative is using a hardware security key. It’s a physical device, typically in the form of a USB dongle, that either requires a tap or insertion during the login process.
You need to physically possess the key to complete this process, which makes it a lot more resistant to phishing attempts and interception (compared to SMS 2FA).
However, not all services support hardware security keys and may not be compatible with them.
You also need to purchase the hardware security key. Unless you’ve set up a backup option, there’s also a risk of being locked out of your account if you lose that key.

Related
I don’t use SMS 2FA for banking and sensitive apps, here’s what I use instead
Time to move beyond SMS codes
Remember that 2FA isn’t foolproof
I am a strong advocate of two-factor authentication (2FA). I’m still scarred from witnessing my friend lose his accounts that weren’t 2FA-locked.
He went through official channels to try to recover his accounts after they were compromised, but they were unable to assist him.
He eventually recovered his accounts by sheer luck. But that shouldn’t happen.
Having an extra layer of protection can go a long way, but you must be selective about how you approach it.
If you use your device to authenticate account access, consider whether it is well-protected and is in your possession only (not a shared device or account).
Creating a strong password that is difficult to crack is just as important. Moreover, if you find remembering complex passwords too tricky, you can always use a trusted password manager to keep everything secure. Or better yet, use passkeys to replace your passwords.
When all else fails, and you’re unsure which option is best, you can rely on multi-factor authentication to tighten your account security.
Source link