On October 3, 2025, Hackread.com published an in-depth report in which hackers claimed to have stolen 989 million records from 39 major companies worldwide by exploiting a Salesforce vulnerability. The group demanded that Salesforce and the affected firms enter negotiations before October 10, 2025, warning that if their demands were ignored, they would release the entire dataset.
The hackers, identifying themselves as “Scattered Lapsus$ Hunters,” a collective said to combine elements of Scattered Spider, Lapsus$, and ShinyHunters, have now published data allegedly belonging to 6 of the 39 targeted companies.
The companies named in the leak are as follows:
- Fujifilm
- GAP, INC.
- Vietnam Airlines
- Engie Resources
- Qantas Airways Limited
- Albertsons Companies, Inc.
What’s In The Data
While the impacted companies are the only ones who can verify the breach, Hackread.com has carried out an in-depth analysis of the leaked data, and it looks legitimate. In all 6 leaks, the record contains personal details of customers, business, including email addresses, full names, addresses, passport numbers, phone numbers,
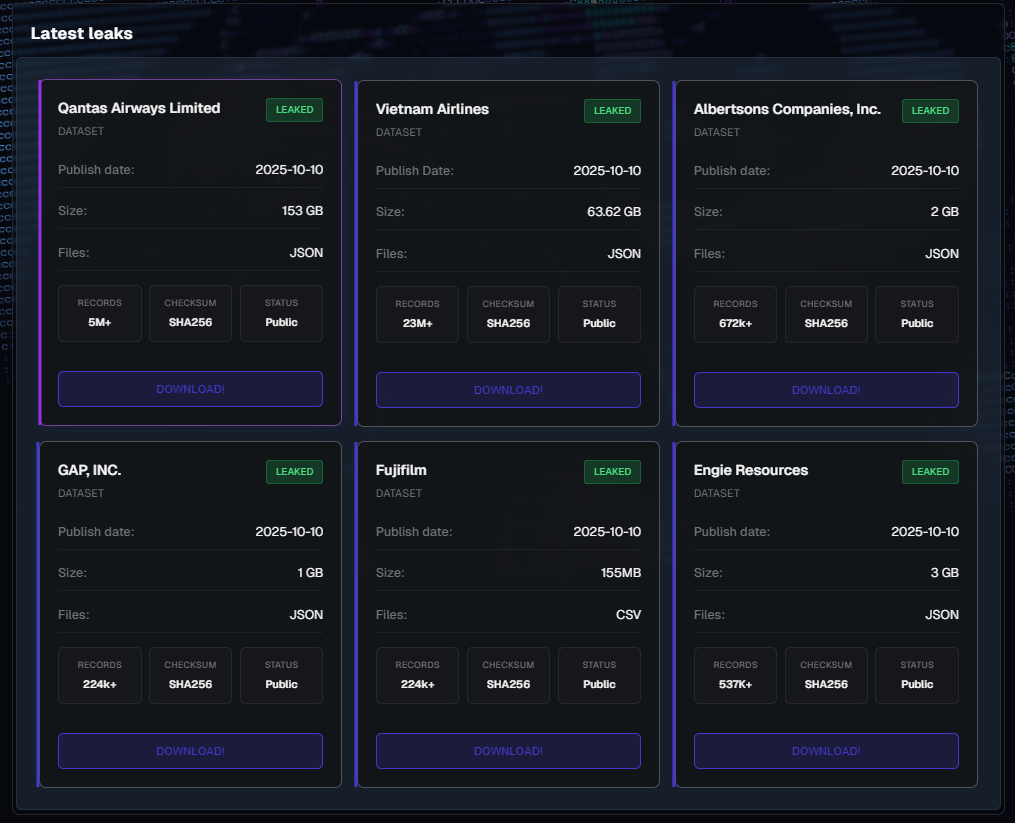
Qantas Airways Limited
The dataset leaked from Qantas Airways Limited is substantial in size, weighing in at 153 GB. The files are in JSON format and contain over 5 million records. The data was published on October 10, 2025, and marked as public by the threat actors.
This dataset combines personally identifiable information (PII) with customer loyalty and internal business data, making it a serious exposure if authentic. Here’s what the leaked data contains:
- Gender
- Country
- Full name
- Date of birth
- Points balance
- Currency used (AUD)
- Frequent flyer number
- Frequent flyer join and anniversary dates
- Title or salutation (for example, Mrs, Mr)
- Frequent flyer tier and status credits
- Phone numbers (main, alternate, home, business, mobile)
- Email addresses (primary, alternate, business, home)
- Account creation and modification timestamps
- Mailing address details (city, postal code, latitude, longitude, etc.)
- Account or customer ID numbers (internal Salesforce and Qantas IDs)
- Profile preferences (for example, meal, seat, marketing preferences, newsletters)
- Membership and loyalty details (bronze tier, expiry, status credits till next level)
- Internal CRM fields (OwnerId, RecordTypeId, CreatedBy, etc.)
- Links to internal reports and templates (for example, “QCC Frequent Flyer Report”, “QCC Lounges Report”)
- Customer notes and remarks fields
- Geolocation data (latitude and longitude of mailing address)
- Activity and contact tracking metadata (last modified, last viewed, etc.)
- Internal flags and status indicators (HasOptedOutOfEmail, DoNotCall, Active, Sensitive_Contact, etc.)
In its security advisory published on 12 October 2025, the company confirmed that data from 5.7 million of its customers was published online following a major cyberattack. It is worth noting that in July 2025, the company had also confirmed a major data breach connected to a third-party vendor, but did not disclose its name at the time.
Vietnam Airlines
Vietnam Airlines’ dataset is 63.62 GB, also in JSON format, with more than 23 million records. Like the others, it was made public on October 10, 2025. The release, if authentic, represents one of the larger leaks attributed to this round of breaches.
These record includes both personally identifiable information (PII) and corporate account data, along with internal airline CRM fields and loyalty program identifiers such as the frequent flyer number. Here is a list of the types of data contained in the Vietnam Airlines record:
- Age
- Gender
- Full name
- Phone number
- Currency used
- Email address
- Frequent flyer number
- Date of birth and year of birth
- Owner and system metadata
- Internal account and contact IDs
- Business or cargo-related fields
- Account type and record classification
- Corporate or business role information
- Corporate and tax information fields
- Company-related email and phone fields
- Last travel and travel-related tracking fields
- Country and city fields (though some are blank)
- Residential address (street and partial location details)
Albertsons Companies, Inc.
The leak associated with Albertsons Companies, Inc. is relatively smaller, totalling 2 GB of JSON files. According to the listing, it contains over 672,000 records. The data was published on October 10, 2025, and labelled as public.
GAP, INC.
The dataset tied to GAP, INC. is 1 GB in size, formatted in JSON, and reportedly holds more than 224,000 records. The information was uploaded on October 10, 2025, with a public status tag, suggesting it is accessible to anyone through the leak portal.
Fujifilm
The Fujifilm data leak appears smaller in comparison, listed at 155 MB and in CSV format. Despite its smaller size, the dataset still allegedly includes around 224,000 records. It too was made public on October 10, 2025.
Engie Resources
The dataset from Engie Resources measures 3 GB and is formatted as JSON files. It is said to include more than 537,000 records, published publicly on October 10, 2025.
Total Number of Companies Impacted in the Breach
The full list of 39 companies identified as victims in the alleged Salesforce data breach:
- KFC – 1.3GB
- ASICS – 9GB
- UPS – 91.34GB
- IKEA – 13GB
- GAP, INC. – 1GB
- Petco – 9.9GB
- Cisco – 5.6GB
- McDonald’s – 28GB
- Cartier – 1.4GB
- Adidas – 37GB
- Fujifilm – 155MB
- Instacart – 32GB
- Marriott – 7GB
- Walgreens – 11GB
- Pandoranet – 8.3GB
- Chanel – 2GB
- CarMax – 1.7GB
- Disney/Hulu – 36GB
- TransUnion – 22GB
- Aeroméxico – 172.95GB
- Toyota Motor Corporation – 64GB
- Stellantis – 59GB
- Republic Services – 42GB
- TripleA (aaacom) – 23GB
- Saks Fifth – 1.1GB
- Albertsons (Jewel Osco, etc) – 2GB
- Engie Resources (Plymouth) – 3GB
- 1-800Accountant – 18GB
- HMH (hmhcocom) – 88GB
- Instructurecom – Canvas – 35GB
- Google Adsense – 19GB
- HBO Max – 3.2GB
- FedEx – 1.1TB
- Qantas Airways – 153GB
- Vietnam Airlines – 63.62GB
- Air France & KLM – 51GB
- Home Depot – 19.43GB
- Kering (Gucci, Balenciaga, Brioni, AlexMcQ) – 10GB
What’s Next?
While more data was initially expected, the hackers announced on Telegram that they will not be releasing any additional information, stating, “A lot of people are asking what else will be leaked. Nothing else will be leaked. Everything that was leaked was leaked, we have nothing else to leak, and obviously, the things we have cannot be leaked for obvious reasons.” This statement leaves the future of the remaining data uncertain.
However, what has already been leaked is damaging enough. If verified, the release of these databases could have serious consequences across several industries. Airlines, retailers, and energy companies store large volumes of sensitive customer and business information, including personal details, contact data, and internal records.
The exposure of such data puts affected individuals at risk of identity theft and fraud, while also creating potential reputational and financial damage for the companies involved. Since these leaks are linked to earlier claims about a Salesforce vulnerability, the incident also raises questions about the security practices of third-party platforms that manage and store such extensive data.