
Proton has launched Proton Authenticator, a free standalone two-factor authentication (2FA) application for Windows, macOS, Linux, Android, and iOS.
2FA authenticator apps are offline tools that generate time-based one-time passwords (TOTPs) that expire every 30 seconds, and which can be used alongside passwords when logging into online accounts, providing the second factor authentication.
Proton is a Swiss technology company known for privacy-focused end-to-end encrypted services like Proton Mail (email), Proton VPN, Proton Drive (cloud storage), and Proton Pass (password manager).
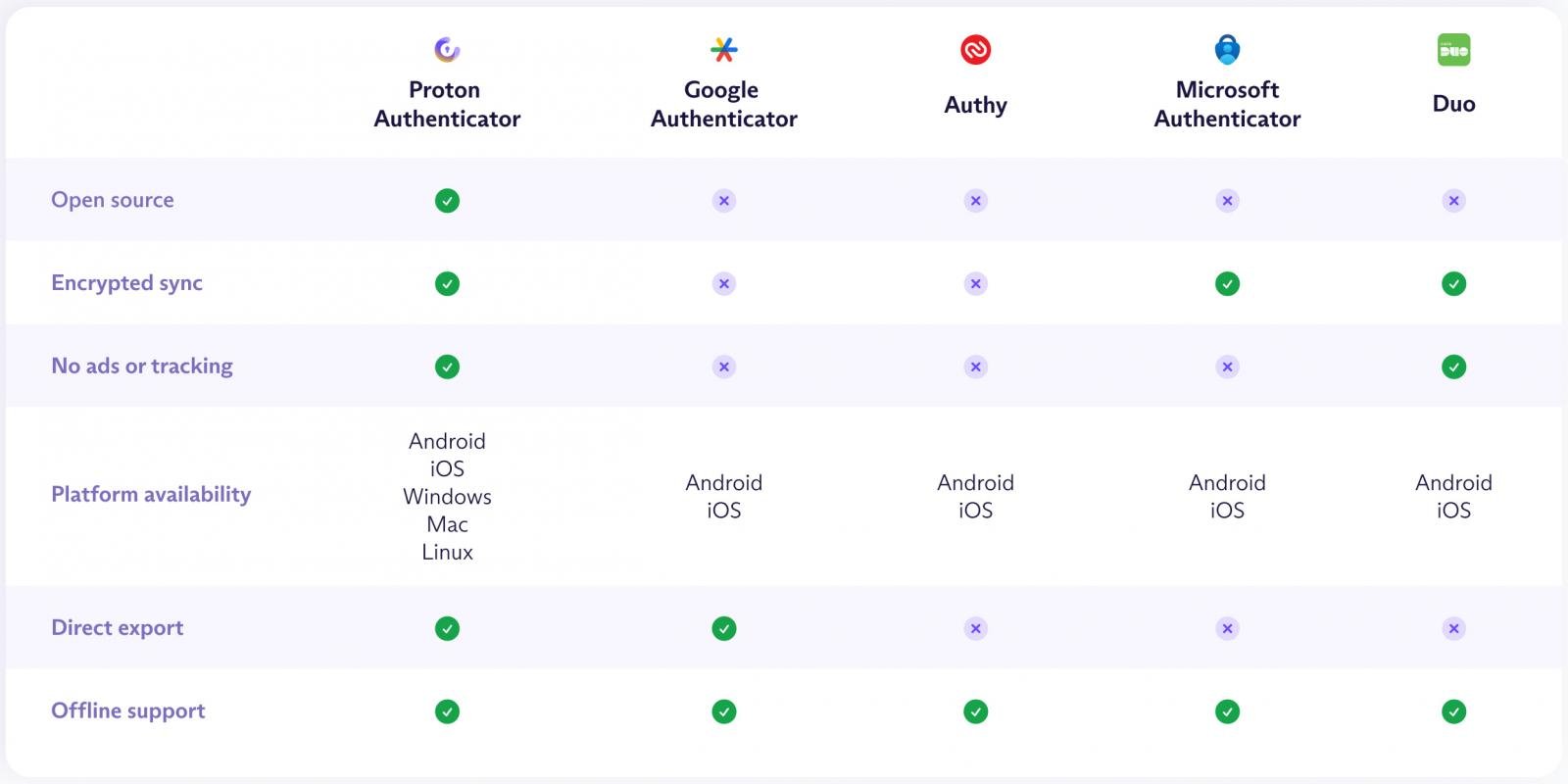
The introduction of an Authenticator app complements the company’s product portfolio and introduces a privacy-focused tool that stands out against competition that is largely closed-source, ad-supported, and locks users into proprietary ecosystems.
Instead, Proton Authenticator uses no ads, trackers, or vendor lock-in, and requires no Proton account.
“Proton Authenticator is built with the same values that power everything Proton does: privacy, transparency, and user-first security,” reads the product launch announcement.
“The company is now bringing these standards to the 2FA space – offering a secure, easy-to-use, and encrypted alternative to apps like Google Authenticator that further lock users into Big Tech’s surveillance ecosystems.”
Source: Proton
The team stated that the app is also open-source, but it typically takes Proton a couple of weeks to release the source code of newly launched tools on GitHub, so we cannot confirm that yet.
Proton Authenticator is built with end-to-end encryption, supporting secure cross-device syncing and migration to or from other platforms through easy-to-use import and export functions.
The ability to export your TOTP seeds is a feature sorely missing from other popular auth apps like Microsoft Authenticator and Authy.
The new tool also offers automatic encrypted backups and app locking with biometrics or a PIN, adding an extra layer of security.
Authenticator apps are significantly more secure than SMS or email-based 2FA because they generate codes locally on the users’ devices. At the same time, the time-based tokens expire quickly, making them useless after a while, even if stolen.
They are nearly immune to phishing, SIM swapping, and man-in-the-middle attacks, as there’s no intermediary that can be intercepted or impersonated.
Hence, if you’re not already using one, it is recommended that you set one up for all accounts that support 2FA protection.
Source link



