Virtual Private Networks (VPNs) have become ubiquitous tools on the internet of today. A VPN creates an encrypted tunnel between your device and a remote server, routing your traffic through that server to mask your real IP address and location. In a sense, it kind of shifts your ISP from your local provider to another, often offshore alternative. Although VPN technology began as a way for businesses to let employees securely access corporate networks in the 1990s, it’s since evolved into a common privacy, anti-censorship, and geoblocking circumvention tool. In fact, one of the first widely used VPN protocols, Microsoft’s PPTP, was introduced in 1996 as a method that enabled encrypted tunnels over the public internet. Fast forward to today, and VPN usage has surged globally.
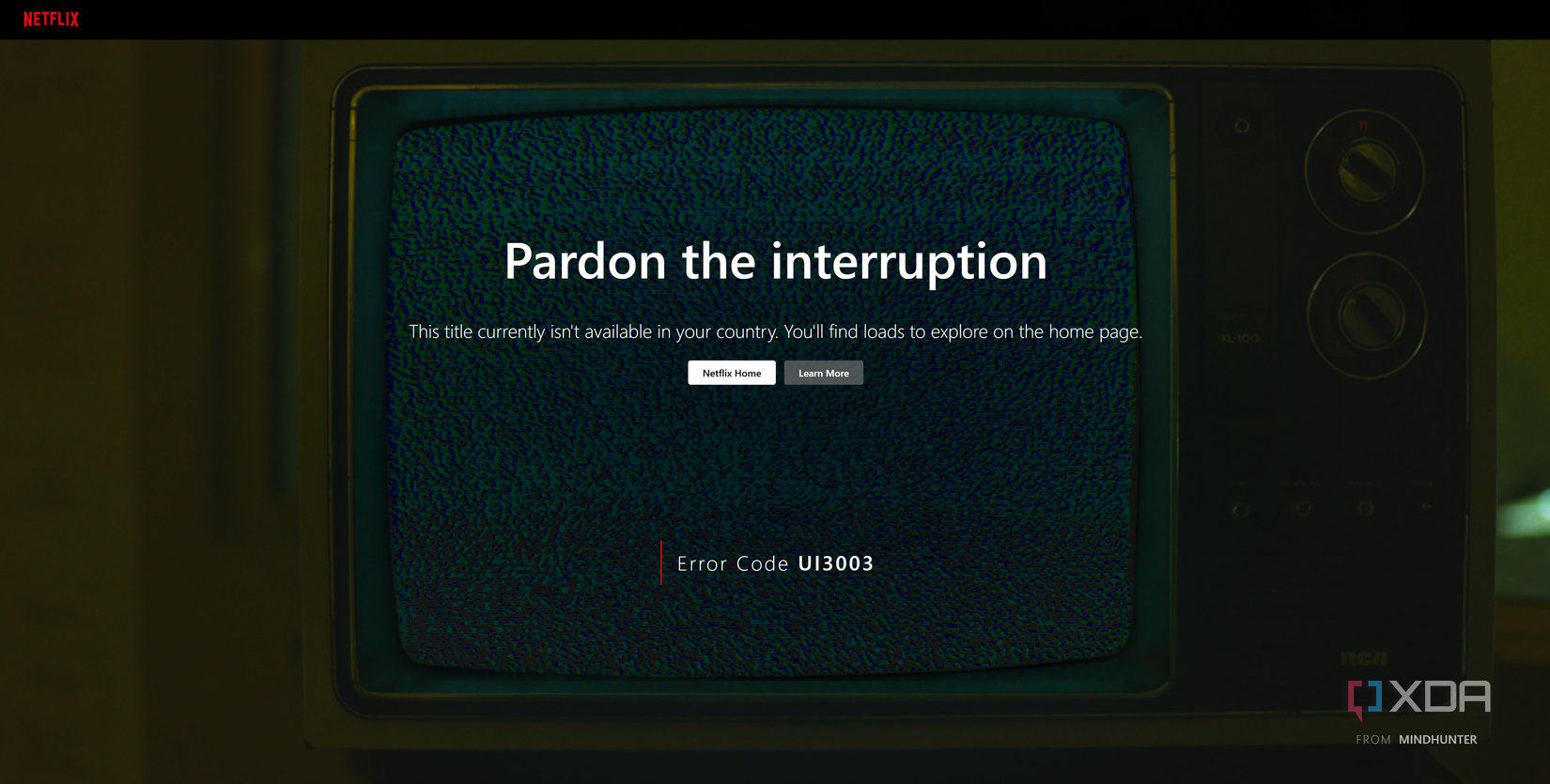
VPNs are essential for a variety of reasons, ranging from circumventing heavy internet censorship and surveillance in many regions around the world to accessing your favorite show on Netflix that’s only available in one specific country. However, many countries engaged in internet censorship ban VPN usage for the purpose of circumventing those blocks, and Netflix itself actively tries to detect VPNs and may only show you globally available content or restrict your access entirely until you turn it off.
Yet you may be wondering, given that a VPN is all about privacy, how do they know? There is a range of measures companies can undertake, from the simple to the sophisticated.
IP address blacklists and geolocation checks
Your IP is in a database somewhere
Every internet connection, whether a VPN or not, exposes an IP address to the destination service. Companies will often analyze the requesting IP address and its associated metadata to gather all kinds of information about the requesting user, and this can include a determination on whether it’s coming from a VPN. IP reputation and blacklists are the first line of defense in this area, and services maintain or subscribe to databases of IP ranges known to belong to VPN providers, cloud hosting companies, or proxy services. If your current IP appears on one of these “VPN/proxy IP” lists, the service can assume you’re using a VPN and block or restrict your access.
Netflix is a company that will often make use of this approach. The simplest technique Netflix uses is checking if your IP is associated with a VPN or hosting provider. Companies like MaxMind compile lists of IP addresses tied to data centers or known VPN servers, and Netflix utilizes such data to blacklist those IPs. They may not specifically use MaxMind, but there are companies out there that exist to compile such lists and sell them to businesses for analytical and security reasons.
Over the years, Netflix and other streaming services have become increasingly aggressive, even banning some cloud data center ranges (AWS, Azure, DigitalOcean, and more) outright since ordinary residential customers wouldn’t typically stream from those networks. Years ago, while I couldn’t stream on Netflix using a typical consumer VPN, I could still stream using a VPN hosted on a dedicated Kimsufi box in France. Eventually, though, that was blocked too, and MaxMind identified it as an “OVHcloud” device.
Banking and financial websites use similar tactics, but for different reasons; mainly fraud prevention. Many banks will flag or even block logins coming from IP addresses linked to VPNs or foreign locations not consistent with the customer’s profile, and in the past, I remember needing to flag to my bank when I intended to travel and what country I would be in so that my account wouldn’t be locked when I logged in. If you normally bank from, say, New York and suddenly appear with an IP in Europe (or one belonging to an Amazon AWS server), the bank’s security system may suspect account takeover or fraud. In fact, some major banks (a notable example being Bank of America) outright block most VPN connections, forcing users to disconnect the VPN to log in. The rationale is that criminals might abuse VPNs to mask their identities, so one way to cut down fraud is to disallow anonymizing networks altogether. The downside, of course, is that legitimate customers traveling abroad or securing their connection are inconvenienced.
Looking past streaming and banking, advertising and analytics companies also monitor IP information to detect VPN usage. There are a couple of reasons for this: these companies are inherently interested in your true location and identity (or an idea of your identity) for both targeting and security purposes. On the one hand, they want to ensure that they’re showing advertisements to relevant users (an advertisement for a European service being shown to an American is a waste of money on the side of the advertiser), and they also want to ensure that click fraud isn’t taking place. Therefore, when you connect via an IP associated with a data center or known proxy, sophisticated ad networks will treat that as a signal that you might be a bot or hiding your real location.
In online advertising fraud detection, distinguishing data center traffic from residential user traffic is incredibly important. IP reputation services, such as IPQualityScore, IP2Location, and more, classify IPs by ISP type and anonymity status. Specifically, flagging an IP as a “hosting provider/VPN” address compared to an ISP-issued residential address. Many websites will respond to a high-risk IP by showing a CAPTCHA, limiting functionality, or simply logging that information for later risk analysis. Both Google and Reddit do this, with the former using a CAPTCHA when a request from a suspicious IP is logged, and the latter seemingly trying to crack down on spam and web-scraping abuse. In short, if your IP address comes from an unexpected source or location, modern web services are quick to notice.
On that note of CAPTCHA, have you ever noticed that some sites, as they require you to solve more and more of these puzzles, seemingly make them harder as you complete them? Maybe they require you to do more of them, or the images get fuzzier, or the text gets harder to read. This is because the site strongly suspects that you’re a bot, and so it throws harder problems at you to ensure that you are a real person.
All of these checks here heavily rely on the expected geolocation of the user or the information associated with the IP address making the connection. Services compare the geolocation of your IP (from GeoIP databases) to the expected location of you or the service you’re accessing. If there’s a mismatch, such as you claim to be an American user in your profile and have used an American payment card, but the IP address accessing the service is registered in another country, it raises a red flag. Even non-security-focused sites may use IP geolocation data to personalize content, and a sudden change can trigger a verification process.
DNS and STUN requests
A sneaky way to check for configuration mistakes
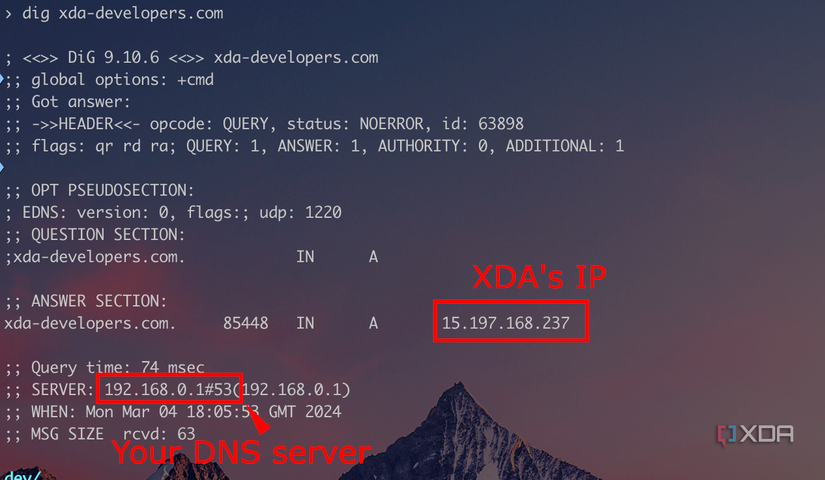
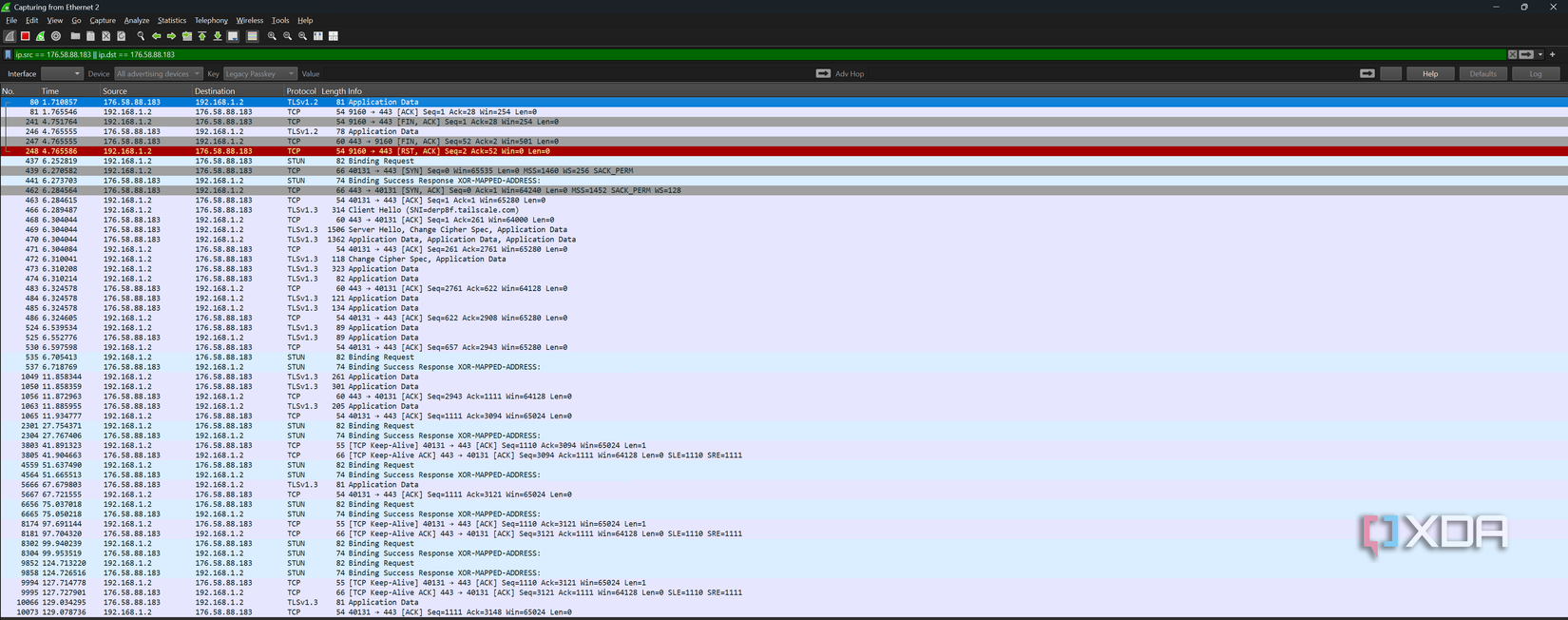
Sometimes, it’s not just the IP address that flags you as a VPN user; it can be the surrounding network clues that give the game away. DNS (Domain Name System) queries are what translate website names to IP addresses. Normally, when using a VPN, your DNS requests are also sent to a DNS server provided by the VPN, keeping them consistent with your new IP location. However, misconfigurations or certain apps can leak DNS requests outside the VPN tunnel, and companies can exploit this. Netflix, for instance, checks for DNS leaks by seeing whether the location of the CDN you requested a video stream from matches your supposed location. If your IP says “London” but your DNS request resolved to a server in, say, Ohio, Netflix now knows that you’re using a VPN.
Generally speaking, DNS leaks are something that any website can watch out for. All they need to do is trigger a DNS lookup (for example, loading an image from a unique subdomain) and see what DNS server resolves it; a site can then tell if that resolution happened through a DNS that doesn’t make sense for your current connection. Your browser might use your ISP’s DNS instead of the VPN’s, and the site may learn your real ISP or region. While VPN providers aim to prevent DNS leaks, they still happen with an improperly configured VPN.
Another sneaky tactic companies can use is WebRTC, though this applies more when your browser is what implements a proxy or VPN, rather than a VPN being handled by your operating system. WebRTC allows for peer-to-peer connections and can reveal a user’s IP through STUN (Session Traversal Utilities for NAT) requests, as many browsers have WebRTC enabled by default. If a site then sees two IP addresses for you, one from your typical connection to the site and one from WebRTC, it’s clear that you’re using a VPN.
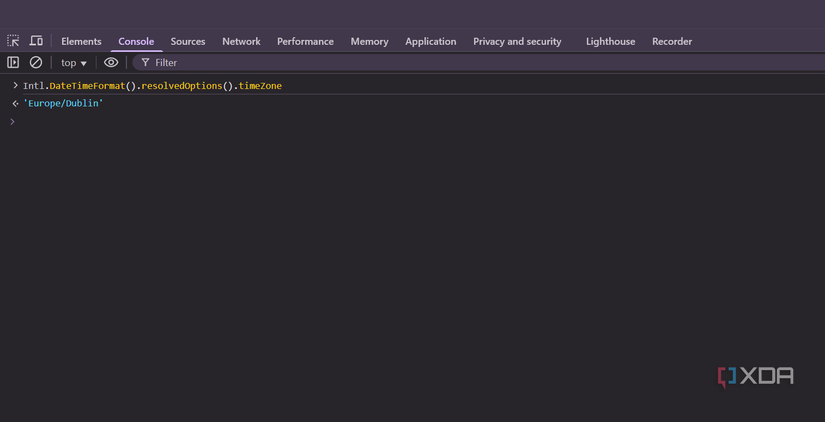
In other words, it’s not just where you’re connecting from that can flag your connection, but rather the inconsistencies that can be associated with your connection. DNS leaks and WebRTC are two common tactics, but even your system timezone can set off alarm bells, as a site can fetch this using JavaScript. You can even try this yourself: turn on your VPN, and type this into your browser console:
Intl.DateTimeFormat().resolvedOptions().timeZone
You’ll see that even though your VPN is switched on, the timezone doesn’t update in your browser. A website can see this, and if it doesn’t match the timezone of the region your IP address is connecting from, that’s another potential leak vector. It’s nowhere near as identifying as your ISP or even your actual IP address, but it can still flag the real country you’re connecting from.
Deep packet inspection
VPN usage has telltale signs
This is where things get significantly more complicated, and it happens at the ISP or government level rather than individual websites. Since a VPN encrypts your traffic and hides its contents, you might assume an ISP wouldn’t be able to tell that you’re using a VPN, but this couldn’t be further from the truth. What is true is that your ISP can’t see what you’re doing inside of the VPN tunnel, like the websites you visit or the data you send, but ISPs can certainly see that a lot of encrypted traffic is flowing to and from a single server, especially if that server is located outside of the country. Essentially, from an ISP’s viewpoint, instead of your traffic going to many different servers and IP addresses with some plaintext traffic dotted through, practically everything is encapsulated and sent to one IP (the VPN server) in an encrypted form. This alone is a pretty strong indicator.
However, Deep Packet Inspection (DPI) is a significantly more intense method of detection, and can be employed in countries where VPN usage is restricted or even outright banned. It’s expensive for an ISP to implement, but a nation-state with a vested interest in preventing VPN usage is likely to have the resources to commit to it. DPI equipment examines packet headers and payloads beyond just the basic IP info, looking for signatures of known protocols and flagging them as potential VPN usage. For example, VPN protocols such as WireGuard, OpenVPN, IPsec, PPTP, and others can potentially be identified by their handshake sequences or byte patterns. For example, OpenVPN uses TLS/SSL, but there are subtle differences in its handshake thanks to its use of an HMAC signature and UDP packets that will make it stand out when compared to regular TLS. A common method of hiding this is to use something like Shadowsocks, essentially wrapping OpenVPN inside another tunnel.
ISPs also have simpler ways to detect VPNs that don’t require DPI. They can maintain their own lists of popular VPN server IPs (just like the websites we talked about do) and take note of whether traffic is going to those IPs. Corporate networks or public Wi-Fi providers often block known VPN port numbers (such as UDP 1194 for OpenVPN, or IPsec ports) or use DPI to disallow VPN protocols so that users can’t bypass their firewalls. For instance, some workplaces or schools will deliberately prevent any traffic that looks like a VPN to ensure you can’t tunnel out and visit disallowed sites.
Even without DPI, an ISP can recognize encryption patterns in packets streaming to and from your connection. Many VPN protocols add characteristic metadata, and examples of this include the IPsec protocol with its identifiable packet headers and older PPTP VPNs, which had easily spotted signatures. WireGuard is another protocol that can easily be detected, as while it focuses on being fast and secure, it makes no attempt at obfuscation.
However, just as websites and VPN providers play cat-and-mouse, so do VPN users and censoring ISPs. There are VPN obfuscation technologies, like Shadowsocks, designed to make VPN traffic look like regular web traffic. There’s also obfs4 (which uses concepts and ideas from ScrambleSuit), and a supporting server can be used as a default bridge to the TOR network. However, packet sequence and size can still potentially flag circumvention, as while normal web browsing will produce varying packet sizes in more random sequences, a steadier sequence of packets from a VPN and consistently high-entropy encrypted traffic might raise suspicion.
In countries where VPNs aren’t restricted, it’s incredibly unlikely that your ISP will employ DPI, and it’s still rudimentary to detect consistent VPN usage. While there are VPN services aimed at countries that restrict their usage specifically, most people don’t need or care for that, and a more off-the-shelf VPN won’t go to such lengths to hide its usage. However, if your ISP looks at your home connection’s logs and sees an hours-long encrypted session to a single server belonging to a hosting provider, it’s a pretty safe assumption that you were probably using a VPN.
Most people don’t need to worry about VPN detection
But it can be hard for those who do need to
VPNs have undoubtedly become mainstream thanks to a combination of the internet privacy movement and online restrictions that have been put in place by some U.S. states and countries like the United Kingdom. However, the attributes that make VPNs useful, like anonymity and traffic encryption, are also somewhat paradoxically what make them stand out the most. Plenty of companies have a vested interest in detecting VPN usage, as do some governments, and it’s important to be aware of what exactly can draw attention to your VPN usage.
It’s a continuous cat-and-mouse game. Each time VPN providers introduce a new way to blend in, such as introducing new IP ranges, stealth protocols, and residential exit nodes, detection systems can step up their game through algorithm refinement and collecting additional data. No single method of detection is foolproof on its own, but combining them all can be enough evidence to flag a connection as coming from a VPN. For the average user, this means that while your VPN can hide what you do online, it’s increasingly difficult to hide the fact that you are using a VPN in the first place. Services may not always care about it, but they are at least aware that it’s happening. Knowing the detection methods is useful as it can help you to understand what information you might be sharing that you didn’t realize.
Companies know a VPN when they see one, by design, and as VPN usage grows, the continuous cat-and-mouse game will continue to play on. Privacy often conflicts with the commercial and regulatory interests of companies and governments alike, and it’s important to know where the weaknesses are. VPNs aren’t a silver bullet to privacy, and there are many other ways you can protect your privacy, too.
Source link